
Orchestration Layer
Simple to use, simple to deploy. Let your systems and technologies work together in perfect harmony.
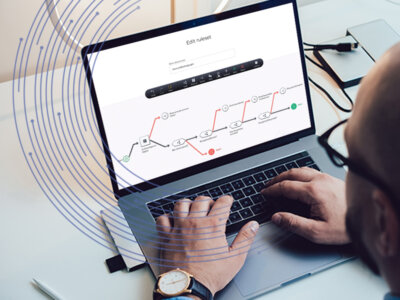
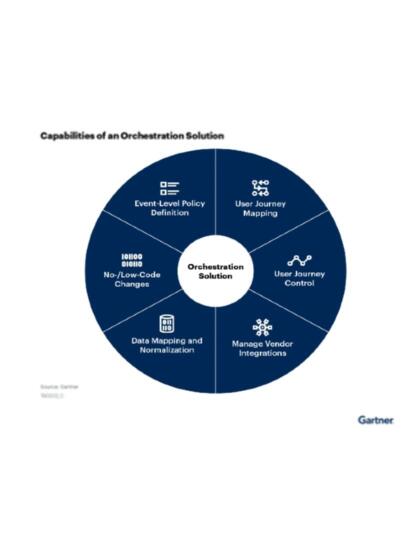
A complete orchestration solution
Security and risk management leaders should reduce complexity in their online fraud detection (OFD) stack and by scaling back reliance on point solutions and instead employing vendor who can deliver value across a range of OFD capabilities through orchestration. (Gartner Market Guide for Online Fraud Detection. ID: G00728937)
Callsign offers a complete orchestration solution. Our multi-model approach exposes multiple levels of data so that you can create dynamic customer experiences in real time.
This enables organizations like yours to deliver tailored customer journeys that balance both risk and experience.
(Gartner, Innovation Insight: Journey-Time Orchestration Mitigates Fraud Risk and Delivers Better UX, June 10, 2022. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved)
Test. Improve. Release. Repeat.

Code-free
integration
Callsign’s Orchestration Layer gives you the power to unite all of your different systems without writing a single line of code.
Our plug and play policy manager and easy-to-use GUI allows you to launch and modify processes and policies, quickly and cost-effectively.
Orchestration
Whitepaper download
Dynamic interventions
Static warning messages are largely ignored – and provide no defence against fraudsters coaching customers to bypass alerts.
Defeat social engineering in real time with interventions that can be tailored to every individual user at any point in their journey – keeping both them and you secure.

A record for
everything
Callsign’s at-a-glance insights and data visualization capabilities bring clarity and understanding to your estate – helping you easily understand and articulate how your systems and data interact, and how they've achieved the desired outputs.
Out-of-the-box templates and regulatory-specific rules including configurable & scalable rulesets make it easy to meet compliance requirements, without having to compromise user experience.
Analyze individual events and ensure that they've been appropriately dealt with
Log and track who did what – and when
Powerful visualization tools make analysis simple
And
there's more...
That’s just the tip of the iceberg. Callsign’s Orchestration Layer has a wealth of other powerful functionalities and features built right in.



